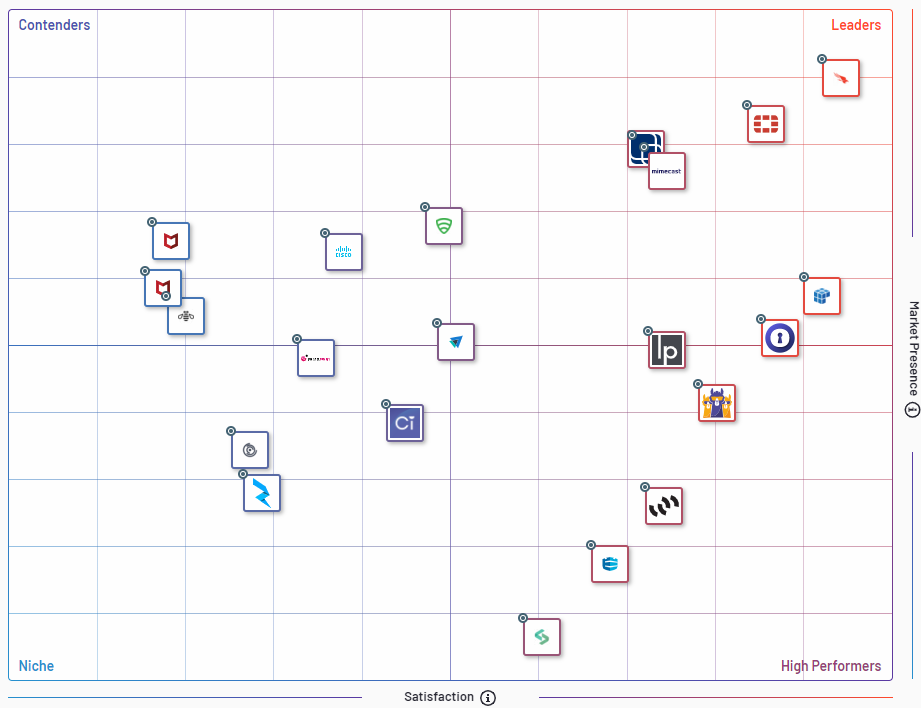
Best Threat Intelligence Software
Threat intelligence software provides organizations with information related to the newest forms of cyber threats like zero-day attacks, new forms of malware, and exploits. Companies utilize the tools to keep their security standards up to date and fit to combat new threats as they emerge. These tools can improve security performance by providing information on threats to their specific networks, infrastructure, and endpoint devices. These products provide information about hazards and how they function, their capabilities, and remediation techniques. IT administrators and security professionals use the data delivered to better protect their systems from emerging threats and plan for possible vulnerabilities. The tools alert users as new threats emerge and provide information detailing best practices for resolution.
Many products like security information and event management (SIEM) and vulnerability management software can integrate with or provide similar information as threat intelligence products. Those products, though, tend to provide live updates and actionable intelligence, and focus on other components of a security ecosystem. To qualify for inclusion in the Threat Intelligence category, a product must: Provide information on emerging threats and vulnerabilities Detail remediation practices for common and emerging threats Analyze global threats on different types of networks and devices Cater threat information to specific IT solutions
Top 10 Threat Intelligence Software
CrowdStrike Falcon: Endpoint Protection | FortiGate | Dataminr | Mimecast Email Security with
Targeted Threat Protection |
Intezer Analyze | Silo by Authentic8 | LogPoint | CrowdSec
| Lookout | Cisco Talos
Compare Threat Intelligence Software
Javawiz Technologies takes pride in showing unbiased reviews on user satisfaction in our ratings and reports. We do not allow paid placements in any of our ratings, rankings, or reports.
Product Description
CrowdStrike’s leading cloud-based Falcon platform protects your systems through a single lightweight sensor — there is no on-premises equipment to be maintained, managed or updated, and no need for frequent scans, reboots or complex integrations. CrowdStrike Falcon’s single lightweight sensor makes it a fast and easy solution to protect your business from cyber attacks. CrowdStrike is widely trusted by businesses of all sizes across all sectors including financial, healthcare providers, energy and tech companies
- Computer & Network Security
- 59% Enterprise
- 33% Mid-Market
ThreatConnect features and usability ratings that predict user satisfaction
Product Description
FortiGate offers a network security platform, designed to deliver threat protection and performance with reduced complexity.
- Network Engineer
- Information Technology and Services
- Food & Beverages
- 71% Enterprise
- 19% Mid-Market
FortiGate NGFW features and usability ratings that predict user satisfaction
Product Description
Dataminr puts real-time AI and public data to work for our clients, generating relevant and actionable alerts for global corporations, public sector agencies, newsrooms, and NGOs. Dataminr's leading AI platform detects the earliest signals of high-impact events and emerging risks from vast amounts of publicly available information. Dataminr's real-time alerts enable tens of thousands of users at hundreds of public and private sector organizations to learn first of breaking events around the world, develop effective risk mitigation strategies, and respond with confidence as crises unfold.
- Marketing and Advertising
- Broadcast Media
- 59% Enterprise
- 34% Mid-Market
CrowdStrike Falcon: Endpoint Protection features and usability ratings that predict user satisfaction
Mimecast Email Security with Targeted Threat Protection
(169)4.4 out of 5 Optimized for quick responseProduct Description
Mimecast Targeted Threat Protection safeguards your organization and employees against sophisticated email-borne attacks. It helps defend against attackers trying to steal data or credentials, plant ransomware, trick employees into transferring money, and springboard to attack supply chains. These kinds of threats require advanced security measures over and above that provided by traditional email security systems.
- Real Estate
- Telecommunications
- 67% Enterprise
- 21% Mid-Market
Dataminr features and usability ratings that predict user satisfaction
Product Description
Intezer automates alert triage, incident response and threat hunting by analyzing potential threats (such as files, URLs, endpoints) and automatically extracts IoCs/hunting rules—providing clear classification and better detection opportunities. Easily integrates into SOC and IR teams workflows (EDR, SOAR, SIEM, etc.) to eliminate most false positives and reduce 90% of alert response time. With Intezer: • Reduce 90% of alert response time • Reduce Tier 1 escalation • Get better detection opportunities • Automate with existing workflow More than 80% of the threats teams deal with are mutations of something already seen. Intezer detects these mutations by identifying any reused code or techniques, helping your team streamline the majority of their workload and stay ahead of attackers. Analyze threats and suspicious files/URLs for free analyze.intezer.com
- Software Engineer
- Student
- 54% Enterprise
- 26% Mid-Market
Mimecast Email Security with Targeted Threat Protection features and usability ratings that predict user satisfaction
Product Description
Silo by Authentic8 rethinks the approach to accessing the web. The Silo Web Isolation Platform executes all web code on secure cloud servers, ensuring web-borne threats never touch trusted assets and online investigations stay secure. By shifting workflows from the endpoint to a remote, high-trust environment, immediately enable risk-free web access, protect sensitive data and conduct online research securely and anonymously. Maintain fully encrypted audit logs and complete policy control over user activity regardless of computer, network or cloud app. Because of these capabilities, more than 500 of the world’s most at-risk organizations trust Silo to completely eliminate the risk of accessing the web
- Military
- Financial Services
- 47% Enterprise
- 28% Mid-Market
Intezer Analyze features and usability ratings that predict user satisfaction
Product Description
Logpoint is the creator of a reliable, innovative cybersecurity operations platform — empowering organizations worldwide to thrive in a world of evolving threats. By combining sophisticated technology and a profound understanding of customer challenges, LogPoint bolsters security teams’ capabilities while helping them combat current and future threats. Logpoint offers SIEM, UEBA, SOAR and SAP security technologies converged into a complete platform that efficiently detects threats, minimizes false positives, autonomously prioritizes risks, responds to incidents, and much more. Headquartered in Copenhagen, Denmark, with offices around the world, Logpoint is a multinational, multicultural, and inclusive company.
- 49% Enterprise
- 28% Mid-Market
Silo by Authentic8 features and usability ratings that predict user satisfaction
Product Description
CrowdSec is a collaborative, free, and open-source Intrusion Prevention System (IPS) software suite. It detects unwanted behaviors in applications & system logs to then enforce remediation at any level (firewall, reverse proxy, etc.) and of any sort (MFA, Captcha, drop, …). Another major strength of the product comes from its user network, where everyone can automatically share aggressive IP addresses that attack them. This collective, highly distributed crowd-sourced threat intelligence (CTI) offers an extra layer of protection. Therefore, CrowdSec combines both behavior and reputation, allowing everyone to have each other's back and form a global cyber defense shield.
- 61% Enterprise
- 24% Mid-Market
LogPoint features and usability ratings that predict user satisfaction
Product Description
Lookout is a mobile app that fights cybercriminals by predicting and stopping mobile attacks before they do harm.
- Information Technology and Services
- Computer Software
- 43% Enterprise
- 43% Mid-Market
CrowdSec features and usability ratings that predict user satisfaction
Product Description
Cisco Talos is a threat intelligence organization dedicated to providing protection before, during, and after cybersecurity attacks.
- Software Developer
- Computer Software
- Telecommunications
- 43% Enterprise
- 35% Mid-Market
Lookout features and usability ratings that predict user satisfaction
Product Description
ActivTrak helps companies unlock productivity potential. Our award-winning workforce analytics and productivity management software provides expert insights that empower people, optimize processes, and maximize technology. Additionally, with data sourced from more than 9,000 customers and over 450,000 users, ActivTrak’s Workforce Productivity Lab is a global center for ground-breaking research and expertise that helps companies embrace and embody the future of work
- IT Manager
- Operations Manager
- Information Technology and Services
- Computer Software
- 61% Enterprise
- 34% Mid-Market
Cisco Talos features and usability ratings that predict user satisfaction
Product Description
For security and intelligence teams, the internet is a critical yet overwhelming source of data for security and threat intelligence. Echosec Systems gives users a single point of access to a diverse range of social media networks, deep web, and dark websites, so they can respond faster and more effectively to real-world events. Our web-based Platform delivers raw data from an unparalleled breadth of online sources in a simple user interface, allowing users to filter out irrelevant data quickly, for a more timely and informed response. Whether the event is a natural disaster, a violent threat, or a planned attack, Echosec Systems offers 24/7 monitoring for immediate alerts and enhanced situational awareness.
- Government Administration
- Legal Services
- 85% Enterprise
- 8% Mid-Market
ActivTrak features and usability ratings that predict user satisfaction
Product Description
McAfee Threat Intelligence Exchange optimizes threat detection and response by closing the gap from malware encounter to containment from days, weeks, and months down to milliseconds.
- Software Engineer
- Computer Software
- Information Technology and Services
- 44% Enterprise
- 39% Mid-Market
Echosec Systems features and usability ratings that predict user satisfaction
Product Description
Cyberint fuses Threat Intelligence with Attack Surface Management, providing organizations with extensive integrated visibility into their external risk exposure. Leveraging autonomous discovery of all external-facing assets, coupled with open, deep & dark web intelligence, the solution allows cybersecurity teams to uncover their most relevant known and unknown digital risks - earlier. Global customers, including Fortune 500 leaders across all major market verticals, rely on Cyberint to prevent, detect, investigate, and remediate phishing, fraud, ransomware, brand abuse, data leaks, external vulnerabilities and more, ensuring continuous external protection from cyber threats.
- 75% Enterprise
- 17% Mid-Market
McAfee Threat Intelligence Exchange features and usability ratings that predict user satisfaction
Product Description
Founded in 2017, Defendify is pioneering all-in-one cybersecurity for organizations with growing security needs, backed by experts offering ongoing guidance and support. Delivering multiple layers of protection, Defendify provides an all-in-one, easy-to-use platform designed to continuously strengthen cybersecurity across people, process, and technology. With Defendify, organizations can streamline cybersecurity assessments, testing, policies, training, detection and response in one consolidated and cost-effective cybersecurity solution. Protect against sophisticated cyber threats with more than a dozen solutions in one place, including: • Cybersecurity Risk Assessments • Technology & Data Use Policies • Incident Response Plans • Penetration Testing • Threat Alerts • Phishing Simulations • Cybersecurity Awareness Training Videos & Graphics • Classroom Cybersecurity Training • Stolen Password Scanning • Network Vulnerability Scanning • Website Scanning • Managed Detection & Response See Defendify in action at www.defendify.com
- 68% Enterprise
- 33% Mid-Market
Defendify Cybersecurity Platform features and usability ratings that predict user satisfaction
Product Description
Check Point’s multilayered security technology provides protection against advanced and zero-day cyber threats, preventing attacks, minimizing risks and offering rapid response
- Hospital & Health Care
- Information Technology and Services
- 58% Enterprise
- 42% Mid-Market
Argos™ Threat Intelligence Platform features and usability ratings that predict user satisfaction
Product Description
McAfee GTI for ESM delivers a constantly updated, rich feed that enables rapid discovery of events involving communications with suspicious or malicious IP addresses.
- 43% Enterprise
- 43% Mid-Market
Check Point SandBlast Network features and usability ratings that predict user satisfaction
Product Description
IBM Security X-Force Threat Intelligence is a security solution that adds dynamic Internet threat data to the analytical capabilities of IBM QRadar Security Intelligence Platform.
- Computer Software
- Transportation/Trucking/Railroad
- 44% Enterprise
- 31% Mid-Market
McAfee Global Threat Intelligence (GTI) for ESM features and usability ratings that predict user satisfaction
Product Description
SIRP is a Risk-based Security Orchestration, Automation and Response (SOAR) platform that fuses essential cybersecurity information to enable a unified cyber response. Through a single integrated platform, it drives security visibility, so decisions can be better prioritised and response time is dramatically reduced. With SIRP, the entire cybersecurity function works as a single, cohesive unit. SIRP combines security orchestration, playbook automation and case management capabilities to integrate your team, processes and tools together. SIRP makes security data instantly actionable, provides valuable intelligence and context, and enables adaptive response to complex cyber threats and vulnerabilities
- 42% Enterprise
- 35% Mid-Market
IBM X-Force Exchange features and usability ratings that predict user satisfaction
Product Description
Maltego is an open source intelligence (OSINT) and graphical link analysis tool for gathering and connecting information for investigative tasks.
- 53% Enterprise
- 32% Mid-Market
SIRP features and usability ratings that predict user satisfaction
Product Description
Zignal’s Narrative Intelligence Cloud analyzes billions of digital stories in real time to help customers discover and manage the narratives that can help or harm them. Used by the world’s largest companies and public sector organizations, Zignal’s natural language processing and machine learning algorithms identify risks and opportunities as they emerge, providing insight into how to contend with the narratives that matter. Zignal serves customers around the world, including Expedia, Synchrony, Prudential, and The Public Goods Project
- Public Relations and Communications
- Computer Software
- 40% Enterprise
- 30% Mid-Market
Maltego features and usability ratings that predict user satisfaction
Product Description
Recorded Future is the world’s largest intelligence company. The Recorded Future Intelligence Platform provides the most complete coverage across adversaries, infrastructure, and targets. By combining persistent and pervasive automated data collection and analytics with human analysis, Recorded Future provides real-time visibility into the vast digital landscape and empowers clients to take proactive action to disrupt adversaries and keep their people, systems, and infrastructure safe. Headquartered in Boston with offices and employees around the world, Recorded Future works with more than 1,300 businesses and government organizations across 60 countries. Learn more at recordedfuture.com.
- 50% Enterprise
- 40% Mid-Market
Zignal Labs features and usability ratings that predict user satisfaction
Product Description
Fast, reliable and secure Cloud CDN with intelligent threat protection
- 45% Enterprise
- 36% Mid-Market
Recorded Future features and usability ratings that predict user satisfaction
Product Description
The First Interactive SOC Platform 90% of post mortems show that the high cost of damage from a cyberattack was avoidable, but no one knew in time to stop it. CYREBRO’s SOC Platform is your cybersecurity central command, integrating all your security events with 24/7 strategic monitoring, proactive threat intelligence, and rapid incident response.
- 91% Enterprise
- 9% Mid-Market
Azure Front Door features and usability ratings that predict user satisfaction
Product Description
SpyCloud proactively alerts companies when their users’ data has been compromised in a third-party breach, and automates the remediation of exposed passwords to keep corporate data, sensitive PII, and financial information safe. We protect over 2 billion employee and consumer accounts for the world’s largest businesses and consumer brands, including half of the Fortune 10, as well as leading tech companies, financial institutions and retailers. They use us to prevent account takeover and thwart online fraud. Our solutions are backed by the most comprehensive and actionable repository of compromised credentials and PII - well over 200 billion assets - recovered using Human Intelligence directly from the criminal underground. This means we get data within days of a breach occurring and share it with customers before it is used to cause harm, typically months or even years before it becomes available on the dark web. Though some refer to us as a 'dark web monitoring' solution, our speed of collection means we're well ahead of the typical dark web scanner/scraper technology. The same breach database also powers fraud investigations, enabling investigators to more efficiently de-anonymize malicious actors attempting to harm businesses and their customers.
- 45% Enterprise
- 45% Mid-Market
CYREBRO features and usability ratings that predict user satisfaction
Product Description
LMNTRIX has reimagined cybersecurity, turning the tables in favor of the defenders once again. We have cut out the bloat of SIEM, log analysis and false positives resulting in alert fatigue, and we created new methods for confounding even the most advanced attackers. We believe that in a time of continuous compromise you need continuous response – not incident response. Our approach turns inward and assumes that you’re already breached and that you’re continually going to be breached, so we take a pro-active, offensive, hunting, and adversarial pursuit stance as opposed to a reactive, defensive, legacy stance with analysts staring at a SIEM console wishing they could detect an APT. LMNTRIX Active Defense is a best in class Managed Detection & Response (MDR) service that detects and responds to advanced threats that bypass perimeter controls. We combine deep expertise with cutting-edge technology, leading intelligence, and advanced analytics to detect and investigate threats with great speed, accuracy, and focus. The outcomes we deliver clients are validated breaches that are investigated, contained and remediated.
- 63% Enterprise
- 25% Mid-Market
SpyCloud features and usability ratings that predict user satisfaction
Product Description
ThreatWorx is a next-gen proactive cybersecurity platform that protects servers, cloud, containers and source code from malware and vulnerabilities without scanner appliances or bulky agents. ThreatWorx serves multiple use cases including threat intelligence, DevSecOps, cloud security, vulnerability management and third party risk assessment.
- Computer Software
- 44% Enterprise
- 33% Mid-Market
LMNTRIX features and usability ratings that predict user satisfaction
- 75% Enterprise
- 25% Mid-Market
ThreatWorx features and usability ratings that predict user satisfaction
Product Description
Falcon X combines automated analysis with human intelligence, enabling security teams, regardless of size or skill, to get ahead of the attacker's next move.
- 75% Enterprise
- 25% Mid-Market
Bitdefender Advanced Threat Intelligence features and usability ratings that predict user satisfaction
Product Description
ThreatConnect, Inc. provides cybersecurity software that reduces complexity for everyone, makes decision making easy by turning intelligence into action, and integrates processes and technologies to continually strengthen defenses and drive down risk. Designed by analysts but built for the entire team (security leadership, risk, security operations, threat intelligence, and incident response), ThreatConnect’s decision and operational support platform is the only solution available today with cyber risk quantification, intelligence, automation, analytics, and workflows combined. To learn more about our Cyber Risk Quantification, Threat Intelligence Platform (TIP) or Security Orchestration, Automation, and Response (SOAR) solutions, visit www.ThreatConnect.com
- Information Technology and Services
- Computer Software
- 125% Enterprise
- 25% Mid-Market
Falcon X: Threat Intelligence features and usability ratings that predict user satisfaction
Product Description
Kaspersky Lab is a Russian multinational cybersecurity and anti-virus provider headquartered in Moscow, Russia, and operated by a holding company in the United Kingdom. It was founded in 1997 by Eugene Kaspersky, Natalya Kaspersky and Alexey De-Monderik. Kaspersky Lab develops and sells antivirus, internet security, password management, endpoint security, and other cybersecurity products and services.
- Information Technology and Services
- Computer Software
- 125% Enterprise
- 25% Mid-Market